- Home
- About
- Services
- Cybersecurity Services
- Our Work
- News
- Contact
Beyond VPN: How Zero Trust Remote Access Protects Your Hybrid Workforce
The New Normal Demands a New Security Strategy
Let’s face it: the way we work has changed for good. Whether your team is logging in from home, a coffee shop, or halfway across the world, remote work is now a permanent fixture. But while flexibility is great for productivity, it’s also a goldmine for cybercriminals, especially if you’re still relying on traditional VPNs.
VPNs were built for a different time. They assume that once someone is inside the network, they can be trusted. But in today’s threat landscape, that’s a dangerous assumption.
This is where zero trust remote access comes in. It’s not just an upgrade; it’s a smarter, more secure way to connect your hybrid workforce without opening the door to unnecessary risks.
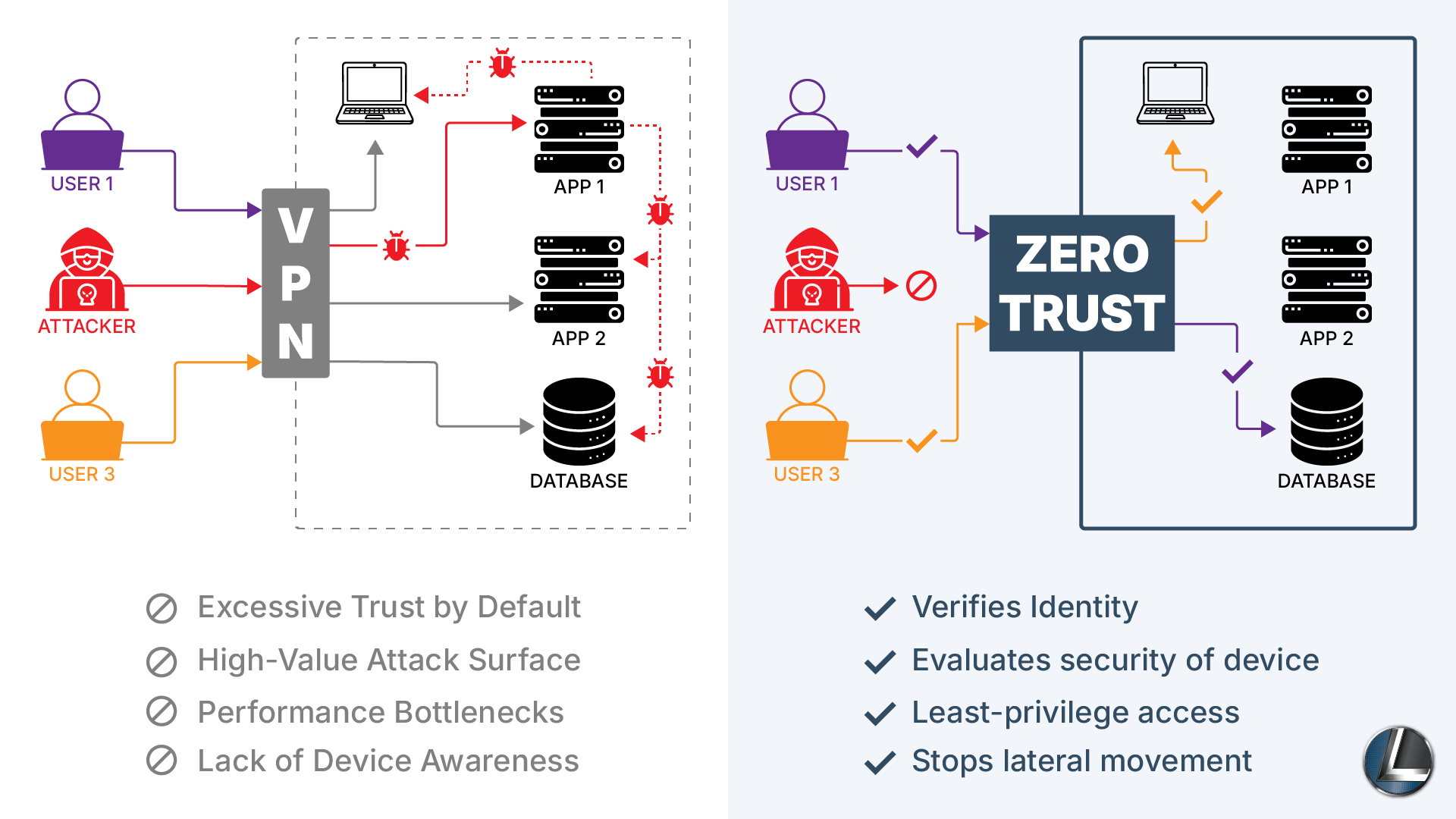
Why Your Traditional Remote Access Is a Liability
Before embracing Zero Trust, it’s essential to understand the risks of relying solely on VPNs for your hybrid workforce:
- Excessive Trust by Default: Traditional VPNs often grant broad network access once a user logs in. If that user’s device is compromised, the entire system becomes vulnerable.
- High-Value Attack Surface: VPN gateways are prime targets for cybercriminals. A single breach can expose every remote user connected through that gateway.
- Performance Bottlenecks: VPNs can introduce latency and connection issues, especially during peak usage, leading to user frustration and reduced productivity.
- Lack of Device Awareness: VPNs typically don’t assess the security posture of connecting devices. An unpatched or infected device can gain access just as easily as a secure one.
According to the Zscaler ThreatLabz 2024 VPN Risk Report, 56% of organizations experienced one or more VPN-related cyberattacks in the last year—a sharp increase from 45% the year before. This trend underscores the growing vulnerabilities of legacy VPN solutions in today’s threat landscape.
What is Zero Trust Remote Access? The “Never Trust, Always Verify” Approach
Zero Trust remote access is built for the way we work today: distributed, dynamic, and constantly connected. As a core part of the broader Zero Trust security model, it operates on a simple but powerful principle: “Never trust, always verify.”
Unlike traditional VPNs that connect users to the entire network, Zero Trust remote access takes a more precise approach. It grants users access only to the specific applications and data they need, and only after confirming that both the user and their device meet strict security criteria. Every login attempt is treated as potentially risky until proven otherwise.
This model hinges on three key factors.
- First, it verifies identity, ensuring the person requesting access is who they claim to be, often using multi-factor authentication.
- Second, it evaluates the security posture of the device, checking whether it’s patched, encrypted, and free of malware.
- And third, it enforces least-privilege access, which is granting just enough access for the task at hand, based on the user’s role, location, and context.
By continuously validating these elements, Zero Trust remote access eliminates the implicit trust that makes VPNs so vulnerable and replaces it with a smarter, more adaptive defense.
Secure and Empower Your Hybrid Workforce
Zero trust remote access does more than tighten security by streamlining how your team works. By verifying every user and device before granting access, it stops attackers from moving laterally through your network, even if a device is compromised.
It ensures only secure, compliant devices connect, reducing your attack surface and keeping internal resources hidden from unauthorized users.
This model also improves performance. Employees get fast, direct access to the apps they need, without the slowdowns and bottlenecks of traditional VPNs. And because access policies adapt in real time based on context like location or device health, your security stays one step ahead.
The Role of Mobile Device Management
Mobile device management (MDM) plays a critical role in this ecosystem. By enforcing security policies on smartphones, tablets, and laptops—such as encryption, remote wipe, and app control—MDM ensures that every endpoint accessing your network meets your organization’s compliance standards.
Getting started is simpler than you might think. Begin by identifying which apps and data need protection. Strengthen identity management with multi-factor authentication, define clear access policies, and choose a Zero Trust Network Access (ZTNA) solution that fits your needs. Start small with a pilot group, then scale with confidence.
The Bottom Line: VPNs Are Out. Zero Trust Is In.
The hybrid workforce isn’t going anywhere—and neither are cyber threats. If you’re still relying on VPNs, you’re leaving the door wide open. Zero trust remote access gives you the control, visibility, and security you need to protect your people and your data—without slowing anyone down.
Empower your hybrid workforce with security that keeps up. Talk to our team today about implementing Zero Trust remote access.
