Property Wide Wi-Fi
Why Spotty Service is Costing You Time and Money
If you own or manage a...
AI Data Breach Examples
AI Data Breach Examples
Every time you asked AI for help, did you unknowingly hand over your...
AI in Business Operations (The AI Gap)
AI in Business Operations (The AI Gap)
The era of competitive advantage being measured by manual...
CMMC Level 1 vs. Level 2 Assessments: A Guide to the New Framework
CMMC Level 1 vs. Level 2 Assessments: A Guide to the New Framework
If your organization works...
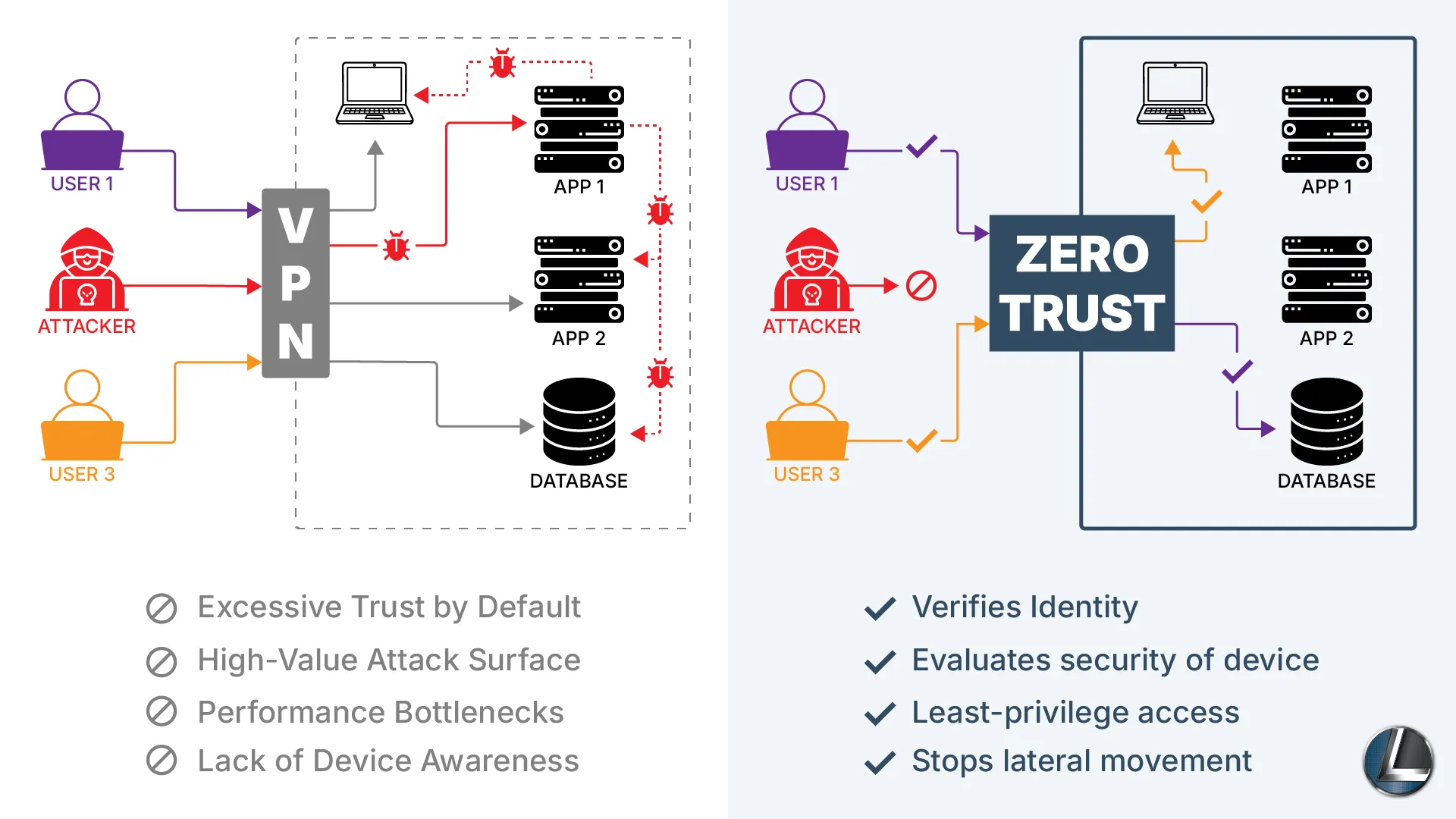
Beyond VPN: How Zero Trust Remote Access Protects Your Hybrid Workforce
Beyond VPN: How Zero Trust Remote Access Protects Your Hybrid Workforce
The New Normal Demands...
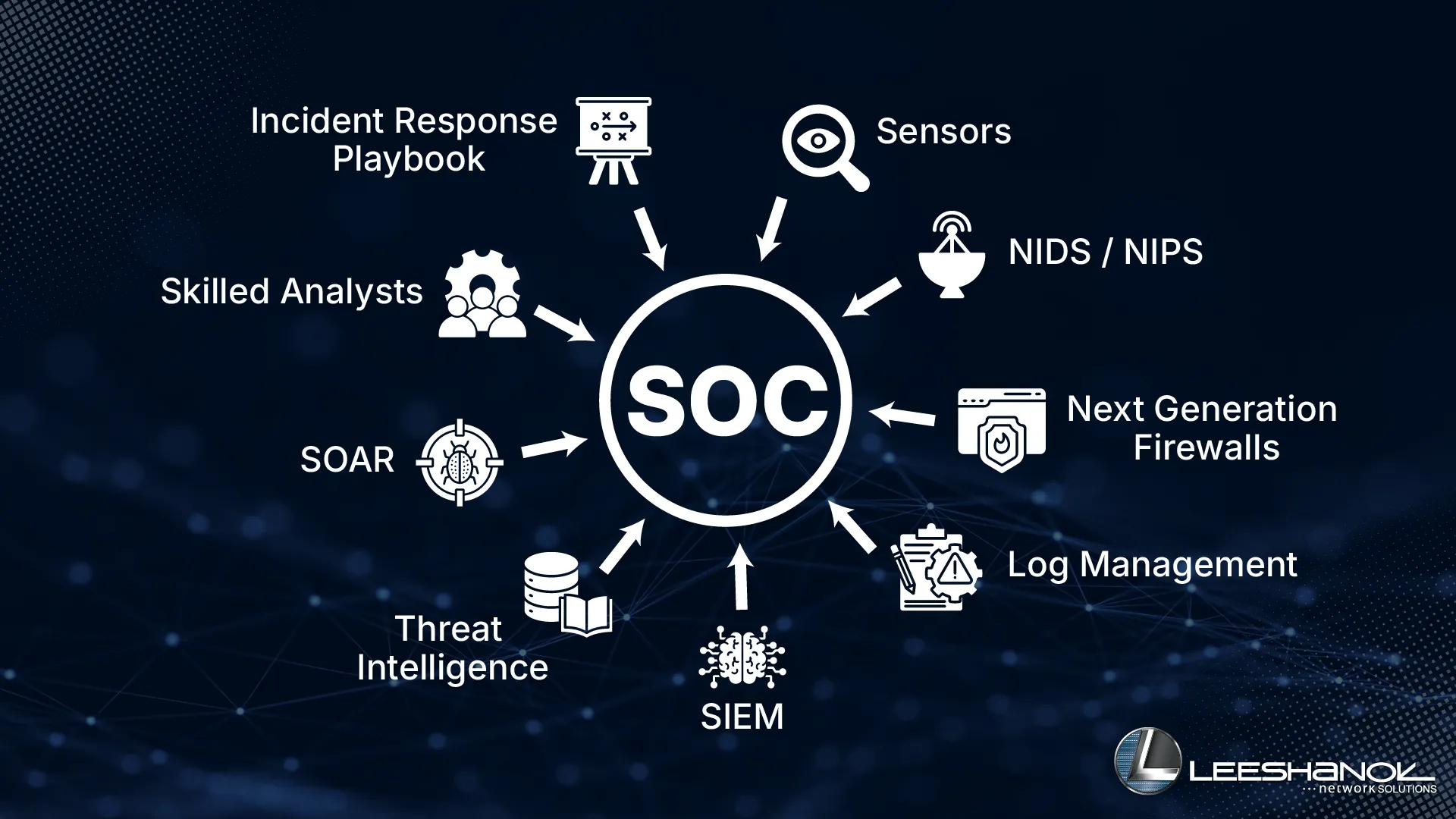
Key Components of an Effective SOC Network: From Sensors to SIEM
Key Components of an Effective SOC Network: From Sensors to SIEM
In today’s digital-first...
5 Essential Tech Tips Every Arizona Business Should Know in 2025
5 Essential Tech Tips Every Arizona Business Should Know in 2025
Doing business in Arizona...
Top Questions to Ask Your MSP in 2025
Top Questions to Ask Your MSP in 2025
As technology continues to evolve at a rapid pace, the...
Decoding the Buzz: Your Comprehensive Guide to Generative AI
Decoding the Buzz: Your Comprehensive Guide to Generative AI
Decoding the Buzz: Your Comprehensive...
Active Defense: The Physical Security Imperative in Cybersecurity
Active Defense: The Physical Security Imperative in Cybersecurity
Modern business security requires...