Implements secure login systems, multi-factor authentication, and role-based access.
- Home
- About
- Services
- Cybersecurity Services
- Our Work
- News
- Contact
- Cybersecurity Services
- Compliance
Comprehensive Compliance Solutions for Arizona
In today’s fast-paced, tech-driven world, navigating regulatory requirements is essential. LeeShanok offers expert compliance solutions to help your organization meet standards like CMMC 2.0, HIPAA, PCI DSS, and NIST.
We go beyond checklists, with specialists integrating seamlessly into your team to deliver practical, tailored solutions. From gap assessments and remediation to proactive monitoring and ongoing support, we ensure your systems, processes, and documentation are audit-ready and secure.
Schedule a consultation and take the first step toward a more secure, compliant future.
Benefits of Partnering with LeeShanok for Your Compliance Solutions Needs
-
![]()
Decades of Experience
LeeShanok has been securing organizations across Arizona since 1997.
-
![]()
Proactive & Strategic Approach
Our methods are deeply rooted in industry best practices to stay ahead of evolving threats.
-
![]()
Rapid & Clear Communication
We act fast, keep you informed, and guide your team every step of the way.
-
![]()
Minimal Disruption to Your Business
We prioritize business continuity while implementing compliant processes.
-
![]()
Local Expertise, Enterprise Capability
Based in Arizona, we offer personalized service with capacity to handle large-scale engagements.
-
![]()
Tailored Response Plans
Each response plan is customized to your unique environment, industry, and compliance needs.
-
![]()
Recovery & Remediation
Restore systems and data while strengthening your environment against future attacks.
-
![]()
Post-Incident Reporting
Full incident summary, lessons learned, and recommendations for improving your security posture.
-
![]()
Ongoing Support
Beyond response, we provide managed security services to help prevent future incidents.
-
![]()
Proven Track Record
Trusted by clients in healthcare, education, finance, government, and other regulated industries.
-
![]()
Legal & Compliance Guidance
Support with reporting obligations and regulatory compliance.
-
![]()
Communication & Coordination
Liaison with stakeholders, law enforcement, and insurance providers if needed.
CMMC Compliance Solutions: What You Need to Know
The Cybersecurity Maturity Model Certification (CMMC) 2.0 helps ensure contractors that are working on DoD contracts are equipped to defend sensitive data and maintain national security.
Revised from five levels to three, CMMC 2.0 aligns each with established National Institute of Standards and Technology (NIST) standards. Your required level depends on the sensitivity of the information you handle.
At LeeShanok, we simplify CMMC 2.0 compliance. Our expert team guides you through identifying gaps, implementing controls, and preparing for audits. We customize solutions to your business, helping you build trust with partners while we handle cybersecurity.
How LeeShanok Helps
Develops incident response plans, drills, and 24/7 monitoring tools.
Conducts risk assessments and creates mitigation strategies aligned with CMMC levels.
Implements encryption, firewalls, secure backups, and endpoint protection.
Performs gap analysis, mock audits, and prepares documentation for CMMC assessments.
Delivers employee security training tailored to CMMC requirements.
Expert HIPAA Compliance Solutions
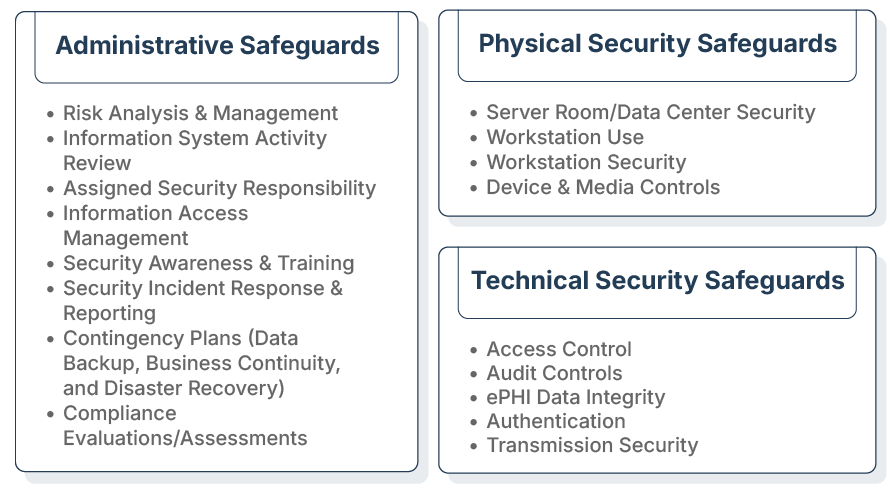
HIPAA compliance is critical for any organization handling Protected Health Information (PHI). Non-compliance can lead to serious legal and financial consequences, but navigating the rules doesn’t have to be overwhelming.
LeeShanok provides expert HIPAA solutions to protect your organization and patient data. We help you understand requirements, implement safeguards like secure infrastructure, access controls, and encryption, and train your staff.
Working closely with your IT and compliance teams, we assess risks, close gaps, and align your strategy with HIPAA’s Privacy, Security, and Breach Notification Rules. From clear documentation to ongoing support, we deliver actionable solutions that strengthen compliance and reduce risk—whether you're audit-ready or building long-term policies.
PCI Compliance Solutions Made Simple with LeeShanok
Accepting credit card payments involves handling sensitive customer data, which in turn demands strong, reliable security. That’s why LeeShanok offers PCI compliance solutions designed to help your business meet industry standards—while preserving trust and ensuring operational continuity.
Moreover, we streamline the journey to achieving and maintaining Payment Card Industry Data Security Standard (PCI DSS) compliance through tailored solutions that safeguard cardholder data and strengthen your cybersecurity posture.
Our PCI compliance solutions include:
-
![]()
Firewalls & Network Security
Safeguard your systems with advanced firewall configurations and continuous network monitoring.
-
![]()
Cardholder Data Protection & Encryption
Ensure sensitive payment information is encrypted and securely stored, reducing risk and exposure.
-
![]()
Vulnerability Management
Identify and remediate system weaknesses before they can be exploited.
-
![]()
Access Control & Authentication
Implement strict access protocols and multi-factor authentication to prevent unauthorized entry.
-
![]()
Network Testing & Monitoring
Maintain visibility into your network with regular testing and real-time threat detection.
-
![]()
Security Policies
Establish clear, enforceable guidelines that align with PCI DSS requirements and support secure operations.
-
![]()
Security Awareness Training
Equip your team with the knowledge to recognize threats and respond effectively, minimizing human error.
Strategic Compliance Solutions from CISM-Certified Experts
Information security and compliance are more than just technical challenges; they are strategic priorities. At LeeShanok, our CISM-certified experts take a proactive, business-focused approach, acting as an extension of your team.
We deliver strategic solutions aligned with global standards like ISO/IEC 27001 and COBIT, ensuring your security initiatives support business goals, reduce risk, and strengthen compliance.

Other Compliance Solutions We Provide
Cyber Insurance
NIST SP 800-171
FTC Safeguards
AICPA SOC 2
ISO 27002
GDPR
Sarbanes-Oxley (SOX) Compliance
Cyber Fundamentals
Our goal is to deliver a streamlined, reliable compliance solution that reduces complexity and keeps your business protected and prepared.
Contact us today to schedule a consultation and take the first step toward a more secure, compliant future.












