This is our second newsletter highlighting the IoT (Internet of Things), a worldwide network of devices that communicate with one another as they collect, analyze, share and store data collected from sensors. This can be beneficial when used by hospitals to monitor patients, and by governments to monitor traffic, pollution or weather. But the balance tips when the collected data is personal in nature or the receiver of the data has unethical or malicious intent.
There are trust challenges with these devices, which tend to have weak or no authentication but which still connect to protected domains. This allows anyone holding one of these devices to gain privileged access to storage, email and cloud accounts, and other aspects of the “secure” network. Here are 4 recommendations to consider:
Select Network Equipment from Magic Quadrant Leaders
Gartner Group’s 2018 report Magic Quadrant for the Wired and Wireless LAN Access Infrastructure lists 3 leaders: Cisco, HP Enterprise, and Extreme Networks. Only these 3 are both visionary with a strong ability to execute. Other providers are visionary, but slow to execute on new ideas, while the rest are followers without much ability to execute.
Cisco Validated Designs (CVDs) provides a design foundation for a broad set of technologies, features, and applications. Every aspect has been thoroughly tested and documented, helping ensure a deployment that’s faster, more reliable, cost effective, and predictable. Check out Cisco’s Remote and Mobile Assets CVD.
Identify Connected IoT Devices
This can be challenging, as devices may identify themselves with cryptic strings and no manufacturer or product identifiers. Device sniffing tools like Angry IP Scanner will provide snapshots of connected devices, and device-visibility software like ForeScout can provide real-time 100% device identification and control. wikiHow details several ways to Identify Connected Devices.
Segment IoT Networks
Splitting a computer network into VLANs (sub-networks) boosts performance and security, both being important as quantities of IoT devices are predicted to surpass PCs and laptops in 2020.
Monitor and Manage Network Traffic
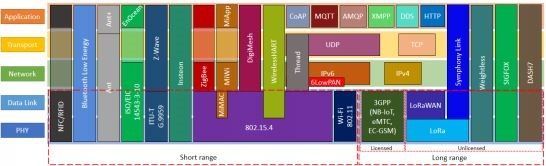
There are tools available to monitor and manage network traffic, but most are focused on performance and reliability. Here is a recent diagram of network protocols used by various IoT industries and use models. As you can see, there is complexity at all layers that must be sorted through to gain understanding. Give LeeShanok a call to help with IoT monitoring and management.
Watch for our next IoT newsletter, where we’ll focus on IoT in select industries, Industrial and Manufacturing environments being one of the first in our series.
Your Technology Partner,
LeeShanok Network Solutions
itsupport@leeshanok.com
Tucson: 520.888.9122 | Phoenix: 602.277.5757
