As federal spending shifts, workforce reductions in cybersecurity agencies are already making waves....
LeeShanok & Deep Sentinel:AI-Powered Security, Real-Time ProtectionEdit
The first layer of cybersecurity is physical security! We’re excited to announce a new offering in...
Malicious OAuth Apps Stealing M365 Credentials
Cybercriminals are actively deploying malicious Microsoft OAuth apps, masquerading as legitimate...
New U.S. Cyber Trust Mark Helps Consumers Choose Safer Smart Devices
The U.S. government has launched a new cybersecurity safety label for smart devices – the Cyber...
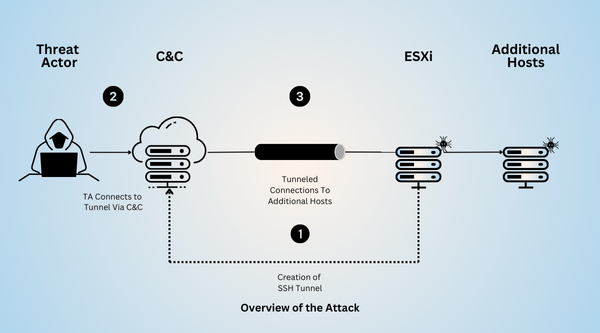
Ransomware Targeting ESXi Hypervisors
Cybercriminals are increasingly targeting VMware ESXi hypervisors, exploiting SSH tunneling for persistent...
Time To Upgrade To Windows 11
Windows 10 is going out of support on October 14, 2025. Using Windows 10 after the end of support...
IT News – 2024 Review: Breaches and Lessons Learned
Looking back on 2024, the threat environment has grown increasingly complex. Several major breaches...
LeeShanok IT News – NSA’s Smartphone Security Tips
If there’s one organization that knows how phones are hacked, it’s the National Security...
The CEO’s Guide to Managed IT
Every day, CEOs, CFOs and their executive teams are faced with tough investment decisions about where...
We’ve Moved!
After 20+ years in our Ft Lowell location, we’re excited to announce that we’ve officially...