Key Components of an Effective SOC Network: From Sensors to SIEM
In today’s digital-first world, cyber threats are more sophisticated and relentless than ever. For your business, the stakes are high: a single breach can cost thousands, damage your reputation, and disrupt operations. Building a strong SOC Network (Security Operations Center Network) is no longer optional—it’s essential.
So, what makes a SOC network effective? At its core, it’s the digital nervous system of your cybersecurity operations, a centralized hub where security professionals, leveraging advanced technology, continuously monitor, detect, analyze, and respond to cyber threats in real time. It’s the mission control for your organization’s digital safety, working 24/7 to keep your business secure.
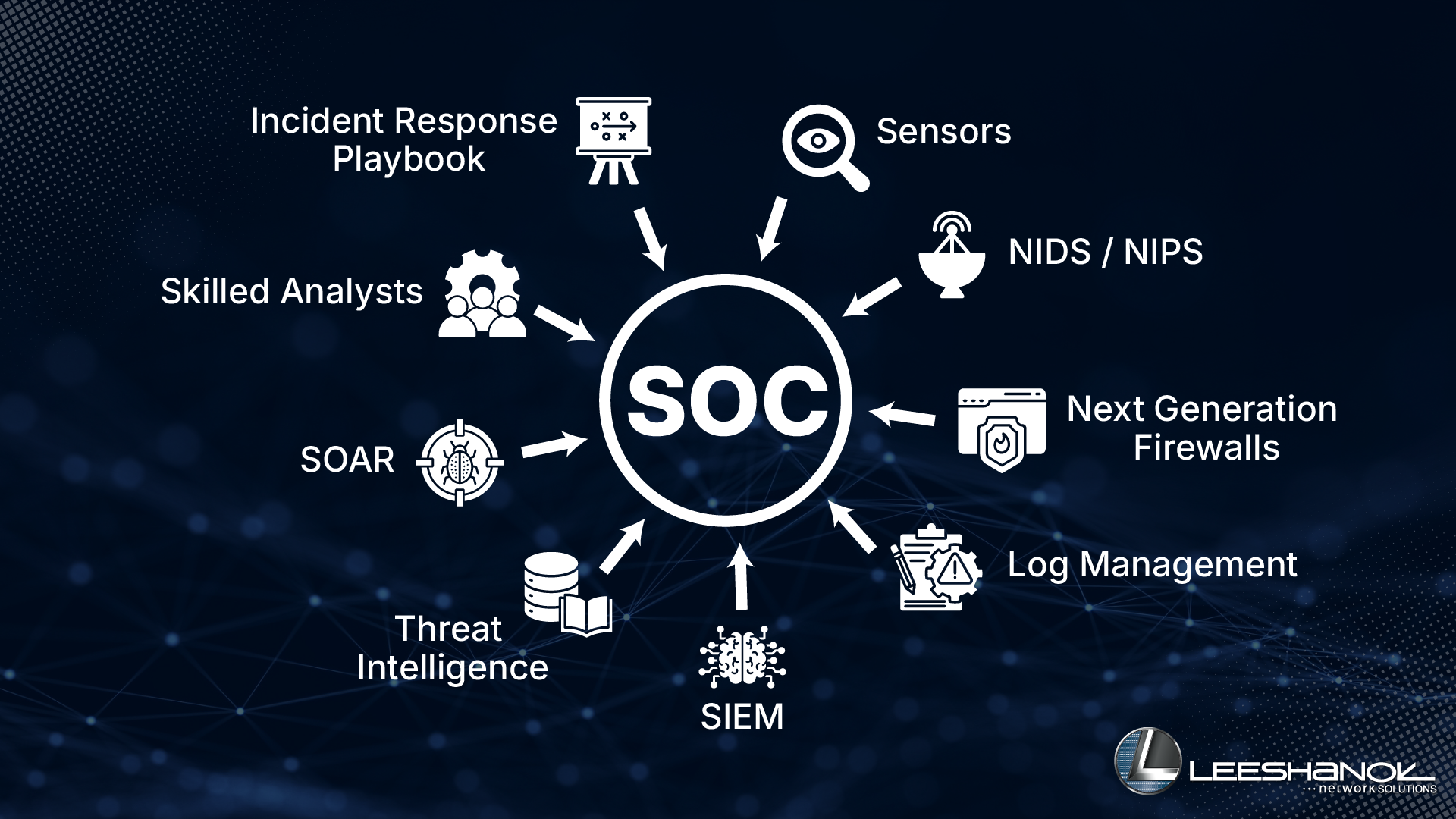
Let’s break down the core components that make up a robust Security Operations Center Network with each playing a vital role in defending your digital domain, from the first line of defense to the final incident response.
The Foundation: Your Data Collection Points
Every effective SOC begins with comprehensive data gathering. You can’t protect what you can’t see!
- Sensors (Extended Detection and Response – XDR): XDR solutions act as highly vigilant security observers, going beyond individual devices to encompass your entire digital ecosystem. They collect and correlate data from a much wider range of sources than traditional endpoint solutions, including endpoints, networks, cloud environments, email, and identities. This comprehensive visibility allows XDR to identify suspicious behavior, unusual file access, or any anomalies across your entire infrastructure. If an attacker attempts to gain unauthorized access through an employee’s computer, moves laterally across your network, or targets your cloud applications, XDR detects these sophisticated threats by piecing together a complete picture of the attack.
- Network Intrusion Detection/Prevention Systems (NIDS/NIPS): While XDR focuses on individual devices, NIDS/NIPS act as vigilant guardians at the network perimeter. They monitor all incoming and outgoing traffic, searching for known attack patterns or anomalies that could indicate an intrusion. An Intrusion Detection System (IDS) alerts you to suspicious activity, while an Intrusion Prevention System (IPS) can actively block malicious traffic, serving as a proactive barrier against unwanted access.
- Next Generation Firewalls (NGFWs): NGFWs surpass traditional firewalls by integrating standard traffic filtering with advanced security like application control, intrusion prevention, and real-time threat intelligence. They identify and manage traffic based on applications, users, and content—not just ports and protocols. Supporting VPNs, URL filtering, and malware protection, NGFWs enhance policy enforcement and mitigate breach risks. As part of your SOC, they offer an adaptive, intelligent first line of defense against evolving cyber threats.
- Log Management: Nearly every device and application in your IT infrastructure generates logs, which are essentially digital records of all activities. From server errors to user logins, these logs contain a wealth of information crucial for identifying security incidents. Your SOC requires efficient mechanisms to collect and store all of this data.
The Brains: Making Sense of the Data
Collecting data is only the first step. The true power of a SOC stems from its ability to analyze that data and transform it into actionable intelligence.
- Security Information and Event Management (SIEM): This is the brain of your SOC Network. SIEM serves as an advanced analytic engine, correlating data from sensors, firewalls, and logs. It links seemingly unrelated events—such as a suspicious login (XDR), unusual network traffic (NIDS), and a failed file access—to detect genuine threats often missed by individual systems. SIEM reduces noise and highlights real dangers for your security team.
- Threat Intelligence Platforms: These platforms serve as dynamic repositories of cyber threats, vulnerabilities, and attack techniques. Cisco Talos, one of the largest commercial threat intelligence teams globally, provides your SOC with real-time insights into global threats, malware trends, and adversary tactics. Integrating Talos enhances your threat intelligence with high-confidence data, improving detection, speeding response times, and keeping your organization ahead of emerging threats.
Hands-On Action: Responding to Threats
Detection and analysis are crucial, but the true value of a SOC Network lies in its ability to quickly and effectively shut down threats. This involves a combination of automated tools and human expertise.
- Security Orchestration, Automation, and Response (SOAR): SOAR functions as the automated response system within your Security Operations Center. When a SIEM identifies a threat, SOAR can automatically trigger predefined actions. For example, if malware is detected, SOAR might automatically isolate the infected device, block malicious IPs, or revoke compromised credentials. This rapid, automated response is crucial for minimizing the impact of attacks before human analysts can intervene.
- Skilled Analysts (Human Intervention & Expertise): Even with advanced automation, cybersecurity remains hands-on. SOC Networks relies on skilled analysts to interpret complex alerts, conduct in-depth investigations, and make strategic decisions beyond automation. These professionals understand evolving threats and lead responses when automation falls short or when critical judgment is needed.
- Incident Response Playbooks: These are your established emergency protocols. For each cyber incident—malware, data breaches, and others—there is a clear, step-by-step plan for containment, eradication, recovery, and analysis. These tested playbooks enable a swift, coordinated response to minimize damage and reduce recovery time.
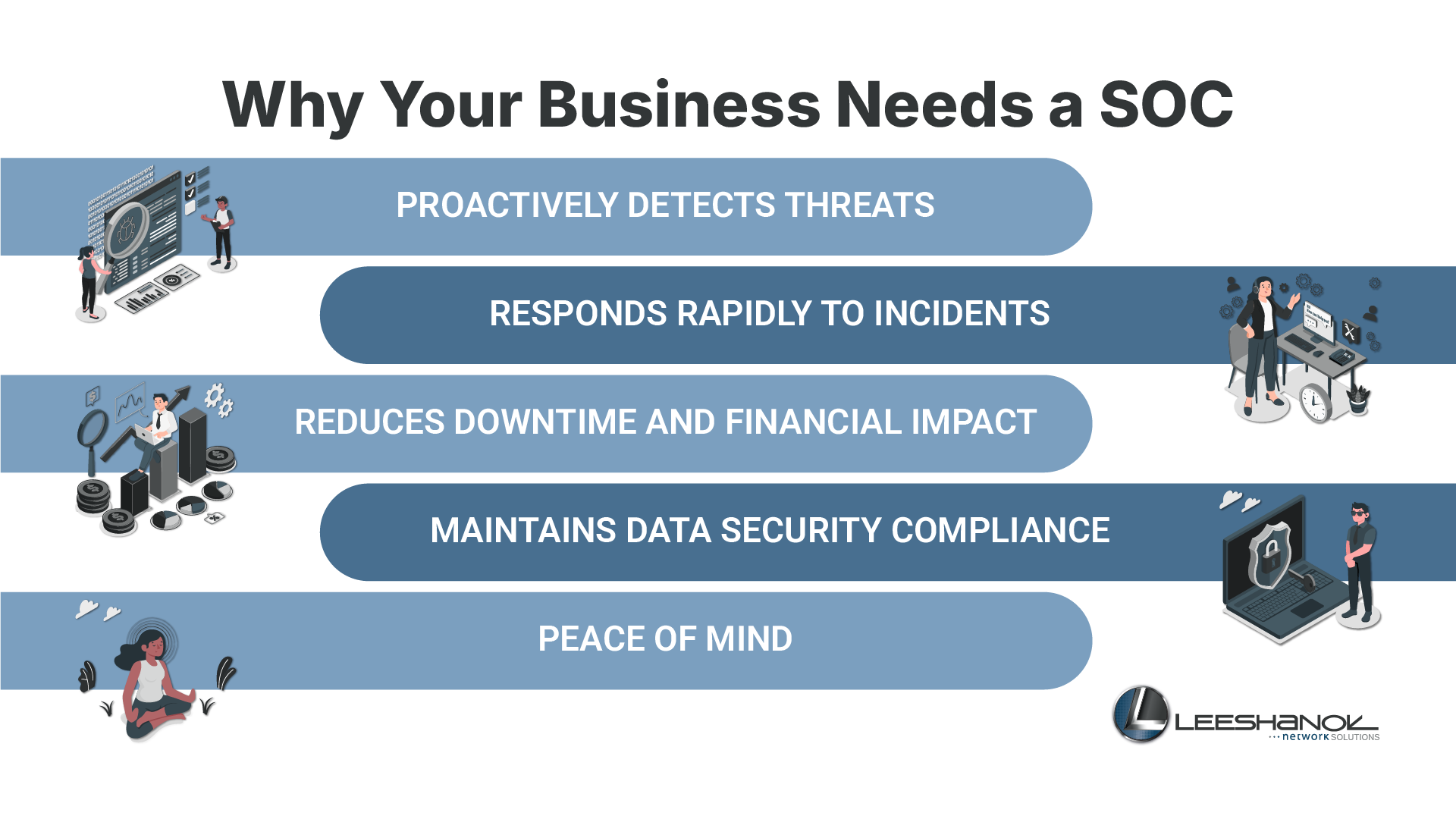
Why Your Business Needs a SOC Network
You rely daily on digital systems—email, cloud storage, customer databases—that are essential to your operations. This reliance exposes you to risks: a single breach via phishing, malware, or unauthorized access can lead to severe financial loss, reputational damage, and penalties. An effective SOC network mitigates these threats by proactively detecting and rapidly responding to incidents, minimizing damage, downtime, and costs. It ensures compliance with data security regulations and protects your critical assets through continuous monitoring, providing peace of mind.
LeeShanok Network Solutions is Your SOC Partner
A 24/7 SOC Network is essential for strong cybersecurity but establishing a full-scale in-house SOC is incredibly complex and expensive. It can take years and substantial investments in infrastructure, specialized software, and a team of expert cybersecurity professionals. That’s why LeeShanok Network Solutions provides 24×7 Security Operations Center services tailored to your needs.
We provide your business with comprehensive 24×7 SOC services, ensuring continuous monitoring, rapid threat detection, and expert incident response.
Ready to protect your business with a powerful SOC Network? Contact LeeShanok Network Solutions today to secure your present and future—so you can focus on growing your business, not defending it.

Copyright © leeshanok.com
Website by CS Design Studios