The Biggest Cybersecurity Threats of Cloud Computing

The cloud offers transformational opportunities. But without proper planning and a trained cloud service provider, you’ll face new cloud security threats. Understanding the biggest cybersecurity threats of cloud computing will help you defend against them.
Cloud Cybersecurity Threats
When you adopt cloud technology, you are giving up the control you have with an on-prem data center. This shift isn’t inherently more or less secure. Some new threats emerge, some threats become less severe, and some threats change.
This guide looks at the biggest cybersecurity threats of the cloud and what you can do to protect against them.
Stolen Login Credentials
For most cloud services, access requires just a username, password, and internet connection. Anyone with these three things could gain access. This makes stolen login credentials one of the biggest cybersecurity threats to cloud computing.
As a result, it’s essential to protect login credentials from data breaches. Password security becomes even more important with cloud services. These are four things you can do to keep accounts safe.
PASSWORD MANAGER
Most people know they need to use strong passwords. They also know they should create unique passwords for every account. However, many still use the same password on many accounts because it’s easy.
Company password managers help employees create and store unique, strong passwords for all accounts. With a password manager, employees only need to remember one strong password. The password manager creates and remembers the rest.
We offer an internal company password manager to clients. We also use and recommend LastPass. Many strong password managers are available.
MULTIFACTOR AUTHENTICATION (MFA)
You should enable MFA on all cloud accounts where possible. This requires employees to authenticate login attempts using their smartphone or other device.
Even if login credentials are stolen, employees can deny unauthorized login attempts using an authenticator app. At LeeShanok, we use and recommend Duo. Google and Microsoft have strong MFA apps as well.
DARK WEB MONITORING
IT needs to be alerted when login credentials are stolen. Dark web monitoring sends an email alert whenever any email address on your company’s domain is detected for sale on the Dark Web.
Once detected, you can immediately ask the employee to change the compromised passwords. LeeShanok offers a free, one-time scan to qualifying Arizona businesses. The scan shows which of your company’s accounts have been compromised.
ACCESS CONTROL
Proper access control policies also protect your cloud systems against stolen credentials. Access control policies can be set within cloud platforms to evaluate every login attempt for red flags. They look for logins from unusual geographies. They can also look for login attempts at unusual times of day. You can also set custom red flags. If enough red flags are triggered, access is denied.
Access control policies can also be set to determine who has access to certain data. For example, your finance department may be the only ones who need financial data. If a non-finance user’s credentials are compromised, the hacker won’t be able to access the financial data.
Internal User Error
Using a cloud service provider makes sure you are working with an expert. Inexperienced users are both prone to error. Bad policies in traditional security solutions can lead to unintended access for employees or too many privileges granted to non-admin users.
Another of the biggest cybersecurity threats of cloud computing is a user accessing data they shouldn’t be. They could accidentally delete data or share confidential info. For data deletion, backups are needed. To stop data sharing, you need a strong data loss prevention (DLP) solution.
SaaS Backups
Most cloud computing solutions offer data backup as part of the service. This has led to a false belief that data on SaaS apps is automatically backed up too. The truth is, native backups on these platforms are limited, leading to cloud security issues. You need purpose-built SaaS backup and disaster recovery solutions to fully recover data stored on these platforms.
For example, Microsoft 365 offers very limited data backup. Data is only stored for a brief period of time (less than one month in most cases), and is only protected if the data loss is Microsoft’s fault.
In other words, if your Microsoft 365 environment is hacked, and you lose data, that data won’t be recoverable without a SaaS backup solution. If your business relies on data from Office applications, you need a specific SaaS backup solution.
For sensitive data, having an on-prem backup solution along with a cloud backup solution is the best bet. With that model, you have a reliable (and affordable) cloud backup, and a quick recovery on-prem backup that you fully control.
Insider Threats
Insider threats are not unique to cloud environments, but they require extra care. In the cloud, data can be accessed by any device anywhere. A poorly configured cloud environment can give employees inappropriate access to data and systems. Those employees may, either maliciously or accidentally, remove that data from your organization.
Thoughtful access control policies minimize this threat by limiting what data and systems employees and contractors can access. You can reduce the likelihood of a breach by walling off sensitive information.
Data loss prevention (DLP) tools also keep sensitive data within the organization. For example, some DLP solutions scan and block outgoing emails and files that contain personally identifiable information (PII) or credit card numbers.
Attacks Against Cloud Providers
Outsider attacks against cloud providers make some IT pros hesitant to move to the cloud. After all, you have more control of on-prem security. With a cloud provider, it’s important to understand who is responsible for what.
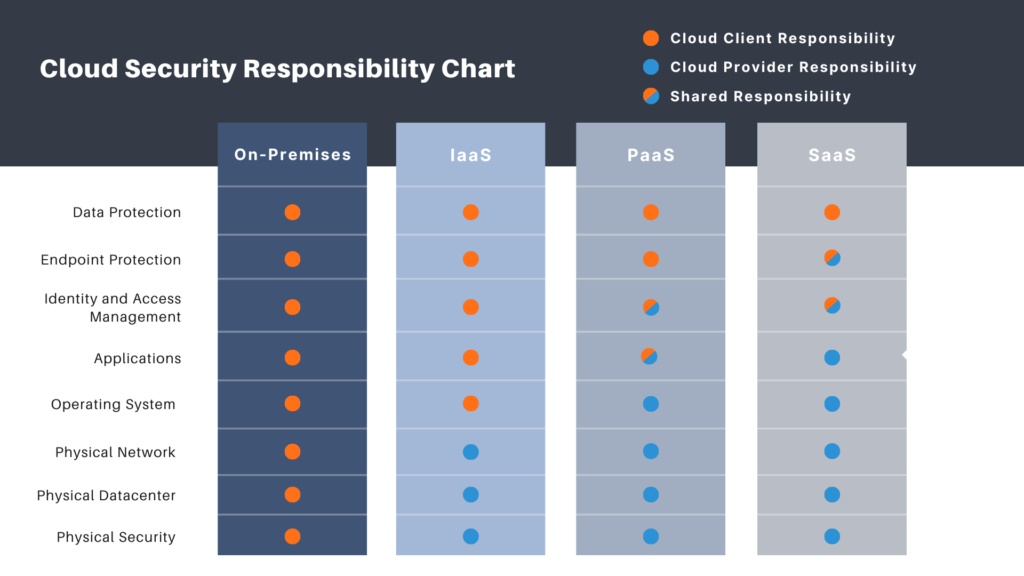
The leading cloud providers invest heavily in security for their platforms. They publish security reports that show how they protect their infrastructure from attacks. Cloud providers have more security resources to than any one business can dedicate to their on-prem solution.
Unfortunately, this is one of the biggest cybersecurity threats of cloud computing that you don’t have control over. However, you can secure your own resources. You can also take comfort in knowing the major providers invest heavily in security. They have multiple contingency plans and fail safes in place.
Lack of Visibility
Migrating from an on-prem environment to the cloud changes the visibility you have into your network. After all, you don’t own the physical hardware in a cloud environment. Your cloud computing platform will give you windows into system status and usage, but full security monitoring may require additional tools.
How do you set up your cloud environment for visibility? Knowing what your security team needs to see is an important first step. Test environments give you a feel for what you will have visibility into.
Shadow IT
Cloud vendors have developed thousands of solutions useful for nearly every department. Department leaders may adopt these solutions without involving IT. Technology used without IT’s knowledge is called Shadow IT. It represents a big cybersecurity threat to your organization.
Say your marketing department needs a better way to engage with customers. They subscribe to a new CRM without involving IT. Now your company’s customer data is on this new platform. But this new platform has not been evaluated for compliance with your cybersecurity policies.
Developing a policy that specifies when IT needs to be involved is the best defense against shadow IT. It’s also important to educate company leadership about the dangers of bypassing IT.
Third Party Applications and APIs
It’s easy to deploy third party apps in your cloud environment. However, shady vendors and oldAPIs create vulnerabilities that hackers try to exploit. You need to give the same care to evaluating software for the cloud as you would for your on-prem data center.
Feeling Unsure About the Cloud?
After reading this, you might be skeptical about moving to the cloud. The truth is the cloud is just like any other technology. It has strengths and weaknesses.
In fact, the cloud may be more secure. Maybe you don’t have what you need to secure an on-prem data center. In that case, you should shift responsibility to a cloud provider. They are better equipped to secure that infrastructure. This makes your data safer in their hands.
The key is making sure your cloud environment is kept safe. LeeShanok has been keeping technology of all kinds secure since 1997. Schedule a consultation with our cloud security experts for a custom roadmap to a secure cloud.

Copyright © leeshanok.com
Website by CS Design Studios