What makes cyber security important? News reports of cyber attacks are coming out more and more frequently. Ransomware has become the tool of choice for hackers looking to extort money from businesses, and email phishing is their preferred method of delivery. The details of each cyber attack are different, but there are commonalities in the results, and it all boils down to risk mitigation.
Victims of cyber attacks suffer damage, including financial loss, ransom demands, unfulfilled orders, missing contractual obligations, and the loss of a good reputation.
Cybersecurity is important because it reduces risk.
Why Protect Against Cyberattacks
Ensure Business Continuity
It’s no secret that cybercriminals are looking to steal money and data when they hack businesses. Most understand this in theory, but rarely consider the full consequences of cyber attacks and what it takes to protect their digital assets against things like identity theft. In the event of a ransomware attack, the costs are more than just the payout of a ransom.
Businesses can also face downtime, expensive recovery costs, notification costs, and costs to properly secure infrastructure once its back online. A relatively small $50,000 ransom could easily turn into $500,000 in associated costs for the business. In fact, an estimated 60% of small and medium sized businesses fail within six months of an attack.
Cybersecurity has shifted from simple antivirus software to an essential information security function to keep businesses operational. Proper cybersecurity makes it more difficult for cyber criminals to execute successful data breaches, and it makes it significantly easier to recover from data breaches when they do occur.
Follow Government Regulations
No company nor individual is immune to cyberattacks, no network or cloud environment is impervious to data breaches, and no business is free from government regulation. These regulations and legislation have been rapidly changing. The law now requires companies to report cyber threats when personal data is exfiltrated or ransomware payments are made following malicious attacks. Companies that don’t comply with these mandates and identify their system vulnerabilities may be subject to fines and other penalties.

Maintain Compliance
Some industries have government mandated compliance standards, like HIPAA for medical clinics. But it’s not only governments that are legislating computer systems’ cybersecurity standards. Companies that accept credit card payments must remain PCI-compliant due to requirements from the credit card industry. Privacy laws like the European Union’s General Data Protection Regulation (GDPR) and California’s Consumer Privacy Act (CCPA) are designed to protect consumer privacy from unauthorized access and cyber crime.
Companies that collect personal information on their customers will be subject to increasing cybersecurity preparedness and requirements for reporting if there is a data breach of that sensitive information. Compliance regulations are likely to become more far-reaching, so companies that invest now in meeting these security requirements for valuable data will be more prepared.
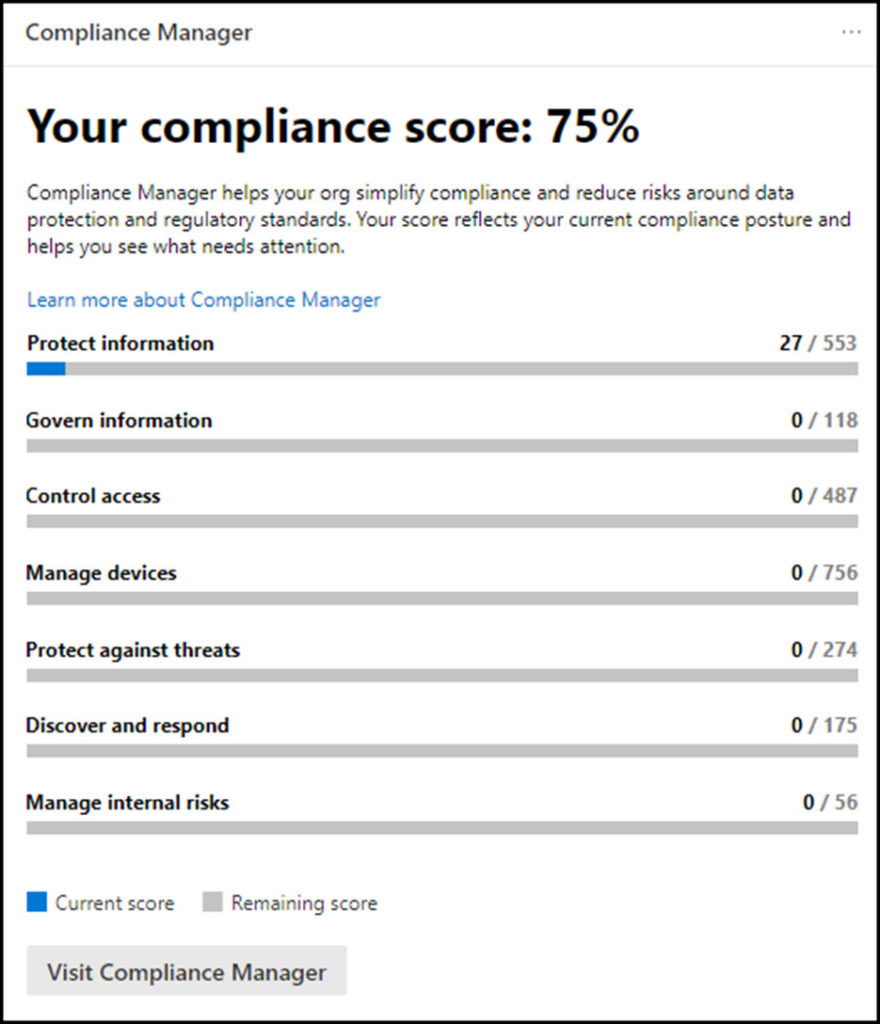
In May 2021 President Biden issued an Executive Order on Improving the Nation’s Cybersecurity. Although the order focuses on the federal government’s security posture and sharing of information between agencies, it also focuses on enhancing software supply chain security and cybersecurity of federal information security analysts. Ongoing compliance is usually dependent on periodic questionnaires with checklist items and less frequent audits that dig deeper for evidence of network security compliance. Tools like Microsoft 365’s Compliance Manager, provide an easy-to-use framework to check your own compliance, along with steps to boost your compliance score and satisfy audit requirements and protect you from future attacks.
Protect Remote Workers’ Sensitive Data
Many employees now work remotely, which means there are more entry points into your network and personally identifiable information than ever before. The sum total of these entry points is your attack surface. The combination of geographic distribution and diverse employee-owned mobile devices increases the attack surface available to global threats. Evaluation should be performed to identify potential entry points so that next-generation firewalls, SSL VPN, and common security configurations pushed out by group policy can be deployed. Zero-Trust policies should be implemented along with conditional access policies to evaluate each access request and apply common security policies. And “geolocation fencing” can be used to prevent attacks from known risky countries or geographies.

Restrict Terminated Employee Access
When some employees learn their employment will be terminated, they begin searching for ways to harm the firm or help their own future. This can include copying company data and contacts for personal or malicious use, and sometimes outright sabotage of their computer or company data. Without proper cybersecurity safeguards against insider threats, companies leave themselves vulnerable to these disgruntled employees.
For example, even when people are let go, most firms don’t change their Wi-Fi passphrase because that would require all remaining employees to modify credentials in all their devices. This oversight allows recently terminated employees to connect to company Wi-Fi while sitting in the company parking lot. There are better ways to manage Wi-Fi credentials such that when a user’s Active Directory account is deactivated, they can no longer connect to the domain or the Wi-Fi network.
Meet Cyber Insurance Requirements
Cyber Insurance is a great tool to mitigate the financial damage of a cyberattack, but each insurance provider has certain cybersecurity policies that must be met in order to obtain coverage. Insurance providers have cybersecurity offerings as stand-alone policies and add-on riders to existing business liability policies. When filling out the application, you’ll find questions relating to cybersecurity preparedness. The insurance companies reduce their risk exposure by making sure the businesses they cover have cybersecurity best practices in place. When filing a claim, the insurance companies may also audit the business for evidence that the cybersecurity practices claimed in the application were still being followed for the claim to be paid out.
Protect Business Reputation
Beyond the financial and legal consequences of a breach, damage to a business’s reputation may be the most difficult to recover from. Trust is one of an organization’s most valuable assets. As an example, consider a healthcare clinic that suffered a breach.
The data the healthcare clinic collects is highly sensitive. Even after the clinic recovers and implements stronger security protocols, patients may be hesitant to return because the clinic failed to protect their information. Vendors, other healthcare providers, and insurance companies may be similarly reluctant to do business with the clinic because of the stain the breach left on the clinic’s reputation. Damage to a company’s reputation is difficult to quantify, but the effects are very real. Beyond protecting data and technology, cybersecurity protects a business’s reputation.
Mitigate Individual Risks
Individuals are not spared either, as email and text based phishing attacks are growing in volume and sophistication. People also tend to use Wi-Fi hotspots where there is little protection between attached devices from multiple customers. Add the fact that many households have installed “smart” devices that are internet connected and that many still use the same password across multiple devices and accounts, and you’ve got a recipe for household chaos or worse.
Improve your Cybersecurity Posture With Managed IT
An alternative to the flawed set-and-forget strategy is a Managed IT plan with a local, reliable cybersecurity and network management provider. Most of these plans have level monthly payments, with shared service level agreements (SLA) that detail responsibilities of the provider and the client firm.
The managed IT provider proactively monitors the health of network devices and updates firmware and software when patches become available. Finding such a provider who has experience with your infrastructure devices and helps client firms comply with industry and governmental cybersecurity and privacy requirements provides huge benefits by preventing cybersecurity incidents and responding to incidents if they do occur.

Summary
Cybersecurity is very important for companies to protect:
- Data stores
- Contact lists
- Identity Theft
- Web accounts
- Access by employees
- Access credentials
- Communication capability (email, SMS, phone, voice mail)
- Company reputation
- Certifications & Compliance
- Customers & Customer Data
- Supply chain partners
Cybersecurity will help protect your company, customers, partners and employees against:
- Operational interruptions (downtime)
- Liability
- Cybersecurity threats
- Unforeseen large labor bills
- Impediments to employee productivity
Ready to Start Investing in Your Cybersecurity?
A great place to start is knowing what has already been compromised. At LeeShanok Network Solutions, we offer a complimentary Dark Web Scan to Arizona businesses that shows all of your company’s compromised usernames and passwords that are for sale on the Dark Web.
