What happens to your data on the computers, printers, and other technology you get rid of? If you’re not careful, that data can be accessed by hackers who are all too happy to “dumpster dive” through your e-waste.
Data “wiped” from hard drives via standard reformatting is still retrievable, and a true DoD-rated software wipe can take days to complete.
Physically destroying storage is the most efficient way to ensure data can’t be accessed. With physical destruction, the hard drive’s platters and microchips are crushed/shredded/sheared so data can no longer be physically retrieved.
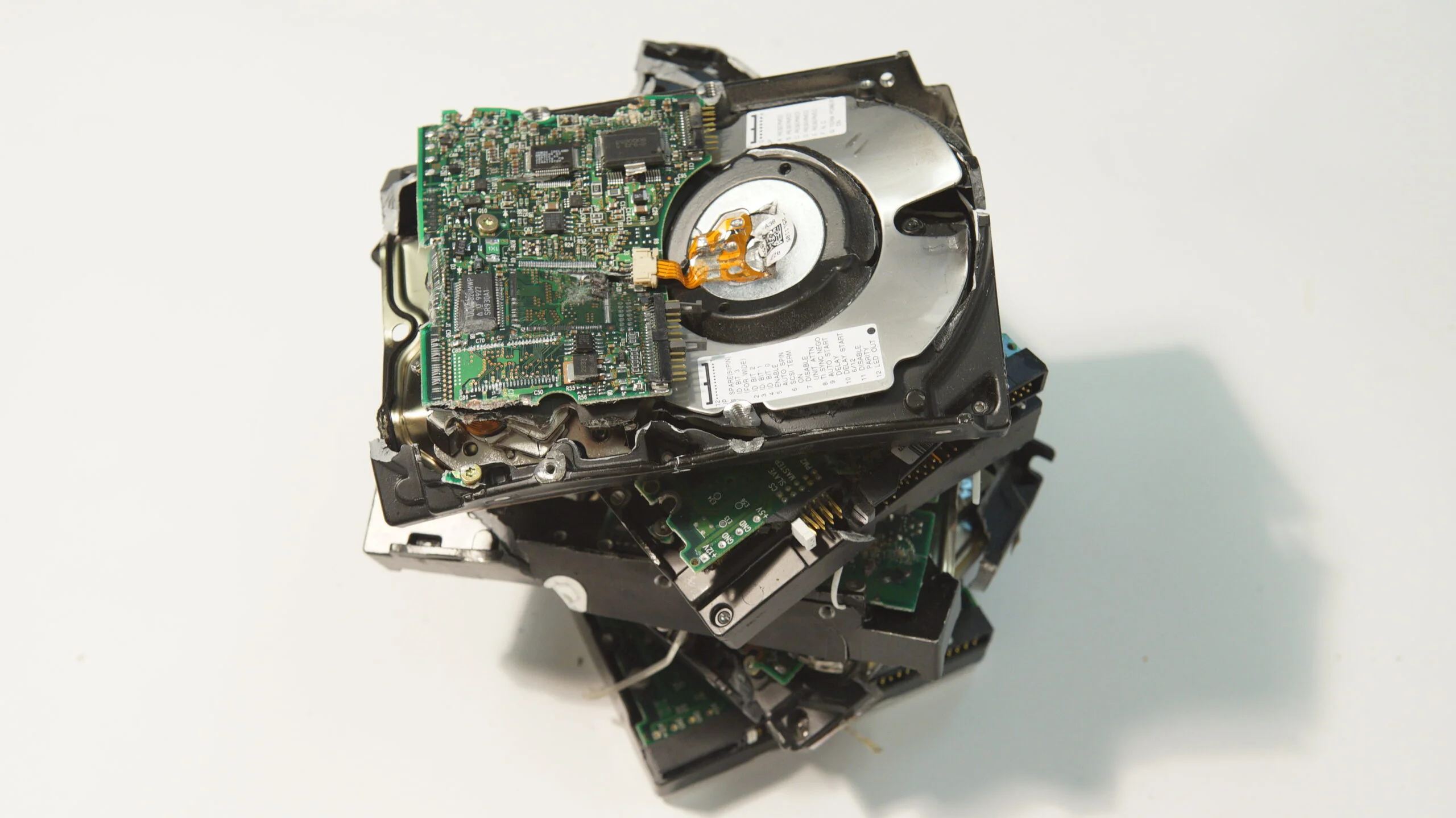
Certified Data Destruction
Regulatory agencies and cybersecurity frameworks are becoming more and more strict about hardware lifecycle management. This means you are increasingly responsible for tracking devices from purchase to destruction.
To prove data was properly destroyed at the end of the device’s life, auditors look for Certificates of Destruction. These certificates ensure data was properly destroyed.
Even if your organization isn’t subject to this oversight, you should still use a destruction service that provides these certificates because not all data destruction techniques are equal.
To help our clients meet these requirements and stay more secure, we’re investing in tools that properly destroy your data and provide you with Certificates of Destruction. Ask your Account Manager for more details!
Security Awareness 101 – New for 2024!

Join our updated IT Security Awareness 101 webinar! We’re covering a host of new topics and old favorites, including:
- Emerging threats from AI
- Social Media Security
- Phishing Prevention
- Password Security
- Latest Scams
- & Much More!
Invite your team for cybersecurity awareness training and enjoy lunch on us via a $20 GrubHuub Gift Card!
Date: Thursday, February 22nd
Time:11am – 12pm
Date: Thursday November 2nd
Time: 11AM – 12PM
Location: Virtual
Topics Covered:
- Social Media Attacks
- Social Engineering
- Phishing Attacks
- Phone Scams
- & Much More!
