Want to learn more about Email from Fake Senders?
First, watch this short video on the Anatomy of an Attack – https://youtu.be/g3lKwgLKL3E.
Let’s say you receive an email message from one of your vendors. When you open it, something doesn’t feel right. The logo below their signature block is fuzzy, and there is an attached file that has “Invoice” in the filename. The sender field shows it was sent from your contact at the vendor. Be careful though, as the sender may be an imposter who has created an email address that looks like your vendor’s email address. The attachment may contain malware to infect your computer and spread through your company’s network.
Let’s review how phishing works and some tips to keep you safe.
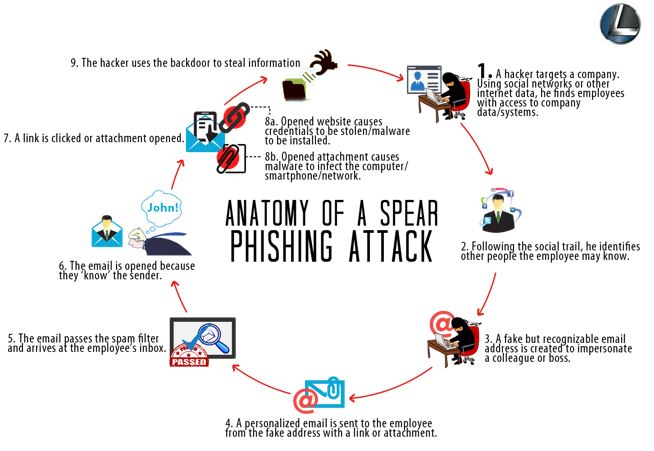
In step 3 above, a fake but recognizable email address is created that looks like a legitimate domain. For example, say bill@qualicart.com is the legitimate email address of your vendor contact. The imposter creates a fake email domain that looks like the original, say he creates “quallcart.com”. Note the 2nd “L” looks like an “I” when glancing quickly. This is similar enough to fool lots of people into opening, clicking, and infecting their computer and network.
qualicart.com –> quallcart.com (look alike domain)
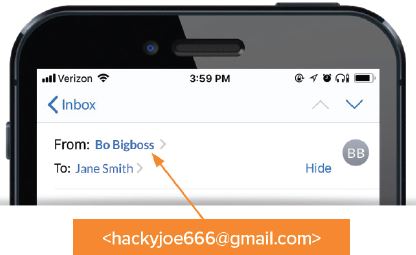
When reading email on a smart phone, it’s challenging to identify spoofed look-alike domains with such small text. To check the actual address on smart phones, tap on the sender’s name and a window will popup showing the actual address or the saved contact.
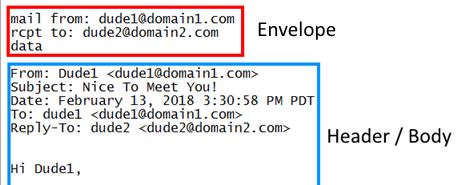
Below is an example where the sender changed the Reply To: (rcpt to:) address, so your reply will be sent to a user at a different email domain. For those who reply rapidly, it makes sense to slow down and inspect where your reply is going to.
Now that you’ve checked the email domain and the address appears legitimate. If the sender is requesting payment, maybe a large payment, it’s time to call the phone number you have on record for the vendor (not the number supplied in the email). Use “human verification” to make sure the payment request is legitimate.
If you would like assistance evaluating an email message, copy the entire message from your Inbox view into Windows Clipboard, then paste the Clipboard contents into a new email message addressed to itrequest@leeshanok.com. We will create a support ticket with the attached suspect email, evaluate if it’s legitimate or spoofed, and contact you with advice.
For a confidential discussion of your IT security situation, feel free to contact us.
Your technology Partner,
The LeeShanok Team
Tucson: 520.888.9122
Phoenix: 602.277.5757
