Access to your company domain and data stores may be controlled by sophisticated next-generation firewalls and access policies. But what about your remote and home-based workers who connect to your Microsoft Azure Active Directory, On-premise Exchange and Exchange Online, SharePoint Online, Teams, or Dynamics using their own devices and sitting in various locations? If they use an older device and connect through a public Wi-fi hotspot, there are numerous risks that your on-premise edge protection never gets the chance to evaluate.
Microsoft now provides Conditional Access controls that provide “zero trust” evaluation of all conditions or signals with enforcement of consistently applied and pre-determined access policies, providing protection from any user with any device at any location using any browser or app and accessing any data store.
Here is a simple model:
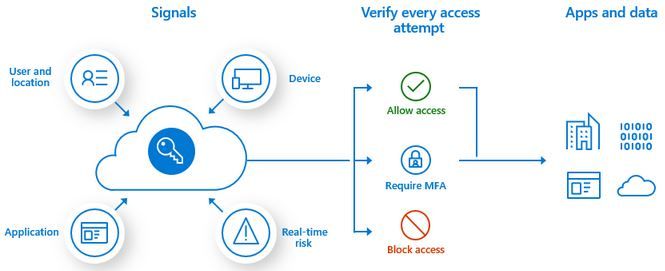
Conditions or Signals can include:
- Sign-in attempt
- User credentials
- Device (including mobile phones)
- Location (example: outside the U.S.)
- Client Apps (examples: web browser, email client)
- Mobile device
Enforced access policies can include:
- Require MFA (multi-factor authentication)
- Block legacy authentication
- Block access by location
- Require compliant devices
- Require compliant operating systems
- Block access except for specific apps
Policy enforcement can require:
- User must satisfy policy BEFORE accessing calling app
- User signs in to calling app, then policy is enforced
This structure can plug holes in out of date (legacy) policies. One legacy policy may allow senior staff members easy access to sensitive data once they’ve authenticated into your domain. This may be fine if they are using their office computer inside your firewall, but what if they are using an old laptop running Windows 7 in a public Wi-fi hotspot? There are multiple vulnerabilities present with this access attempt. Serious risk would also occur if that employee’s credentials were stolen, which an imposter could then use to gain access to the domain for easy access to anything, including your most sensitive data.
Zero-trust Conditional Access evaluates every connection attempt regardless of privilege, and after the condition or signal is evaluated successfully, the access policy is applied to that user’s connection, and if successful they are granted access to certain data by the app, device, and location being used for that one session.
This may sound inconvenient to senior staff whose time is valuable, but it happens very fast and is mostly un-noticeable. One common policy is to require MFA for every access attempt, regardless of user, device, or location. In today’s world where staff may work in the office, from home, at a restaurant, or the airport, it controls every access attempt according to policies that make sense for your business.
Requirements may include additional Microsoft licenses, however, these may already be bundled with Microsoft/Office 365, Azure AD, Intune, or Enterprise Mobility and Security Suite licensing that you already own.
- First, contact your account manager at LeeShanok to let us know you’re interested
- We will determine if you’ll need additional licensing, but many of our managed client firms already have all that’s needed
- Our team will ask you some questions, gather information, and design your Conditional Access
- Finally, we’ll set up the controls and implement the designed structure
From then on, you can be more at ease with the increased security to your domain, accounts, apps, and data.
Your technology Partner,
The LeeShanok Team
