Last Monday Microsoft released a special update to patch security issues considered Critical with Internet Explorer and Microsoft Defender. These vulnerabilities could enable a hacker to take control of a system. The Cyber Infrastructure (CISA) branch of US Department of Homeland Security considered it important enough to announce.
CVE-2019-1255 – Updates automatically, run Windows Update – Microsoft Defender Denial of Service Vulnerability could allow an attacker to prevent legitimate accounts from running legitimate system files. This security update addresses the vulnerability by ensuring Microsoft Defender properly handles files.
To check the Malware Protection Engine version, click [Start] > [Windows Security] > [About], and look for the Engine Version of 1.1.16400.2 or later which is good. If you see 1.1.16300.1 or earlier, you need to apply this update.
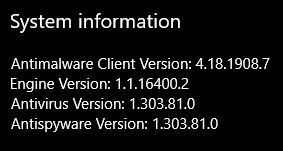
To manually get the new Engine Version, run Windows Update, press [Windows Key] + [R], then type “control update” and press [Enter]. Then Press [Check for Updates], and be sure to reboot when it completes if you’re asked to. If “control update” doesn’t work in Windows 10, repeat and type “ms-settings:windowsupdate” instead.
To check and update the Engine’s Virus Definitions, [Start] > [Windows Security] > [Virus & threat protection] > [Check for updates].
CVE-2019-1367 – Manual update for Internet Explorer 9, 10, 11 – This vulnerability could corrupt memory so that an attacker could run arbitrary code in context of the current user, and if the user is logged in with administrative rights, they could take control of the affected system. This update addresses the vulnerability by modifying how the scripting engine handles objects in memory, and will be included in the October 2019 Patch Tuesday release. This update should be downloaded from Microsoft and manually installed.
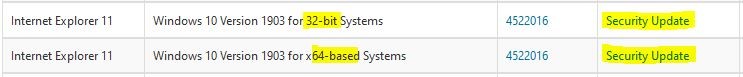
You’ll need the following information to select the correct download.
Operating system version (e.g. Windows 10 Version 1903), press [Windows Key] + [X], then left click [System] and look for “Windows specifications”.
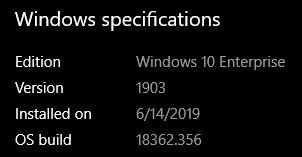
In the same window, look for “System type”.

Finally, to determine the version of Internet Explorer installed, press [Windows Key] + [R], then type “iexplore” and press [Enter]. Click [Help] > [About Internet Explorer].
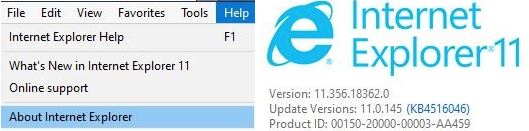
Now you have enough information to download and install the correct patch for this vulnerability. After most updates and patches from Microsoft, a reboot is needed.
For a confidential discussion of your situation or a competitive quote, give your Technology Partner a call.
The LeeShanok Team
Tucson: (520) 888-9122
Phoenix: (602) 277-5757
