With traditional email phishing campaigns, one of the best ways to recognize and delete such messages is whether you know and trust the sender. But what about email messages from your customers, partners, suppliers or fellow employees? You may regularly receive email messages from a contact, so you feel safe opening the email and its links or attachments.
Not so fast! Even if your staff has received cybersecurity awareness training, your customers, partners and suppliers may not have. If their email account is compromised, the attackers can review previously sent messages and develop a timeline for sending invoices and legitimate communication with other firms. Then they copy or create a similar email message, timing it with previous email sends, and out it goes to the contacts expecting such emails. Since it was sent from a known email account, and the email appears exactly like previously received emails, the receiver has little reason to expect anything amiss.
Usual phishing signs may be missing in Business Email Compromise (BEC) messages:
- The sending email account is legitimate, not spoofed, so it gets through spam filters
- The subject of the message matches previous messages from the sender
- The body of the email matches previous messages
- Links & attachments match previous messages
- There is no unusual language or misspelled words, because this message was copied or crafted from previously sent messages
So what can you do?
You can always seek “human verification” before opening attachments or clicking links. Call the sender at the phone number you already have, not the number in the message. Let them know you received the email, and you’re making sure it’s legitimate. If they did not send the message, notify them it appears to have been sent from their email account, then delete the message.
Even if they confirm sending it, you can still proceed carefully. In the email message, right-click on the attachment and click “Save As”, then save the file to your file system. Using Windows File-Explorer, locate the file, right-click, and click “Scan with Microsoft Defender”. If you have a 3rd party antivirus, you’ll also have the option to scan with that app.
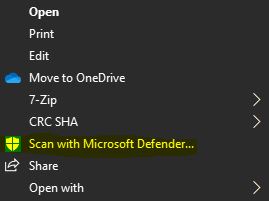
If the scan comes back with “0 threats found”, you can have more confidence it doesn’t have malicious macros inside.
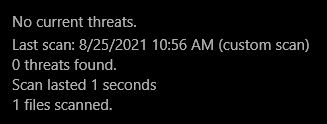
However, whenever you open an attached Microsoft Office file (may be inside attached Zip file) and a security warning pops up, NEVER click “Enable Content”. Instead close Excel & delete the file if you saved it, then delete the email that contained the attachment.
Customers, partners, suppliers & fellow employees are part of our “communication chain”, and we should all watch out for one another. The FBI published an overview of this scam, and steps to protect yourself at https://www.fbi.gov/scams-and-safety/common-scams-and-crimes/business-email-compromise
NEXT STEPS: If you’ve received an email message you’re not sure about, contact our team and we’ll let you know if it’s malicious.
If you regularly communicate with other firms, their potential lack of security preparedness can impact your firm. Encourage them to contact us & we’ll help them assess their own cybersecurity to keep you both secure.
Want to better recognize and handle threats to your data and devices? Register for our free cybersecurity webinar series “IT Security for the Common Worker 101 A & B” at https://www.leeshanok.com/news/events/
Your technology Partner,
The LeeShanok Team
Phoenix: 602-277-5757 | Tucson 520-888-9122 | itsupport@leeshanok.com
