How to Improve Cybersecurity
IT cyber security is designed in layers. Digital threats to a company usually originate from outside. Threats that breach a layer tend to settle in and seek other devices at the same layer. When the attempt to breach the next layer is made, malicious programs will make attempts from multiple devices. By the time inner layers are breached, many devices have already been compromised, and exfiltration of company data has probably already occurred. See Why Cybersecurity is Important.
With network infrastructures that include both on-premises and cloud-based infrastructure, layering your network cybersecurity to protect it all can be challenging. Historically this would require unique solutions for each part of the infrastructure, but today there are solutions available that simplify and consolidate monitoring and management. There are many ways to protect against threats. Below are actionable ways to improve your firm’s cybersecurity.
End Users & Devices
Protect Wi-Fi Network Access from Cyberattacks
Many firms have both staff Wi-Fi and guest Wi-Fi networks. There’s usually a password required to connect to the staff Wi-Fi, but many times the guest network has no password. This opens the door for direct cyberattacks against connected devices. Use a password on all your firm’s Wi-Fi networks.
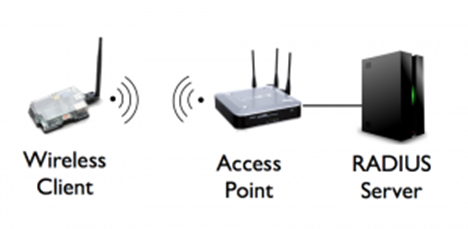
Another issue emerges with Wi-Fi authentication when an employee is terminated. The terminated employee could park close by and connect to the guest Wi-Fi (open) or staff Wi-Fi network (Wi-Fi password still the same), where they could launch attacks against other connected devices or seek company data to steal.
Most firms do not change the Wi-Fi password on termination of an employee because it requires all remaining employees to change the password in the devices they connect with. As time goes by, more and more terminated employees will have access to the company’s Wi-Fi networks. Adding a RADIUS Server to your Wi-Fi authentication fixes this by coordinating with the user’s Active Directory (AD) account. When an employee is terminated, simply marking their AD account “inactive” prevents them from connecting to the Wi-Fi network. No other employee’s access is affected.
Security Measures on Mobile Devices
Regardless of operating system, many employees use personal mobile devices to read company email, log in to cloud accounts, generate and send quotes, and other tasks that require access to company networks and data.
These employee devices may not meet sophisticated cybersecurity measures the company demands from connected devices, and are therefore vulnerable to external access and cyberattacks. If an employee loses their device, all the data and stored credentials may be available to cyber criminals.
To guard against these risks, it’s important for companies to use a Mobile Device Manager (MDM) and enroll all personal phones that are used for company business. Good MDMs push group security policies to enrolled devices, and also locate or wipe a lost phone. Employees should also set up “Find My Phone” while they have the device in their possession so that lost devices are easier to recover.
Utilize Group Policies for Cybersecurity
Group policies are central rules that can be applied to all devices that access company resources. Common cybersecurity policies can be designed for all user accounts and devices at time of login. Policies can also be designed by groups. For example, senior management devices have different cybersecurity rules than front-line workers.
Pushing out cybersecurity policy in this fashion eliminates the need to sit at each device and configure its security in case of a security breach, and it provides common security policies to all employees with certain job types or common access to specific data stores.
Improve Employees’ Password Management
Many employees have a favorite password they never forget, and they use it across multiple websites and their domain login. A data breach at just one of those sites, and all the employee’s accounts are compromised. A better strategy is to use a different password on each site, but that can be impossible to remember without writing them down, another risky practice.
The best strategy is to use a company-wide password manager that generates complex passwords and provides access to password folders via role-based policies. Some password managers provide segmentation of each user’s passwords with their own secure folder, allowing them to manage both their personal and professional passwords. With this strategy, your employee only needs to create and memorize one strong password for the password manager.
Enable Multi-Factor Authentication on All Your Accounts
Enabling two factor authentication for adds a layer of protection to each user account’s sensitive information on personal devices. When logging in, after the username and password are accepted, the site sends a text or notification to an authenticator app on your phone. If you verify the notification, then the connection is completed.
Strong authentication is particularly useful in squashing security risks like a stranger’s attempt to access one of your online accounts and trying to steal your personal data. You would receive notification about a login attempt but did not initiate it. That would be a good time to change the account password to a different strong password, as it’s clear someone has the current credentials or personal information.
Individuals can reduce their cyber risk by enabling MFA on many individual sites, but a faster way is to have your IT department or your managed IT service provider require it for all accounts.
Require Cybersecurity Training
The user is the most important security measure, and an educated user fortifies all other layers of security. Up to 95% of cybersecurity breaches are the result of human error, so it’s important to have all employees regularly trained on cybersecurity best practices.
Keep your business safe with one of the many webinars and in-person trainings are available, but it’s important to select a provider who is knowledgeable and has invested in the quality and delivery of the material.
LeeShanok’s IT Security for the Common Worker series is a free, monthly webinar that teaches cybersecurity best practices to employees of all levels of IT skill. LeeShanok also offers custom, in-person training to Arizona businesses.
Local Network Infrastructure
Assess Your Network Infrastructure and Security
Before making changes to your network, it’s important to assess what you currently have and create a network diagram if one does not exist already. Making changes without understanding the current network layout can result in additional complexity and reduced security.
If you’re not sure where to start, most managed IT service providers (MSPs) offer network assessments that generate documentation of the infrastructure, credentials, configurations, and recommendations to improve security.
Some MSPs like LeeShanok also offer network security assessments, which includes network assessment documentation, along with analyses of the security posture and risks that are present. A network security assessment may also include penetration testing to test actual vulnerabilities.
Segment Your Network
If you have two Wi-Fi networks (like a staff and guest network), segmenting the two into VLAN 1 & VLAN 2 provides a security barrier. Devices and sessions running in one VLAN are blocked from accessing devices in the second VLAN. Network segmentation can be physical or logical and involves breaking down a network into smaller subnets.
Segmenting your public Wi-Fi architecture and maintaining software updates helps simplify management of firewall policies, reduces the overall attack surface, and strengthens your firm’s security.
Proactively Manage Infrastructure
It is very important that the cybersecurity of your network not be a set-and-forget exercise. Even the best defenses see reduced protection over time as bad actors test for and identify vulnerabilities. Many smaller firms use home-grade devices, resulting in big security holes for sophisticated breach strategies.
It is challenging and expensive for internal staff to continuously manage these risks, which is why many use a “set and forget” strategy. Professional Managed IT Service Providers solve this by specializing in proactively securing, fixing, and updating technology more affordably than additional internal staff.
Consider hiring a Managed IT Provider if your internal resources aren’t able to regularly research and deploy new cybersecurity strategies to keep up with the evolving threat landscape.
Replace Legacy Devices
Improve your cybersecurity posture by replacing aging devices with new devices that have more sophisticated and coordinated security features. Work with your internal IT or your managed IT service provider to select new devices that align with your overall IT strategy.
Following deployment, it is also important for you or your managed service provider to actively manage infrastructure components, keep their firmware and software up to date, and investigate all notifications when threats are detected.
Update Firmware and Software in All Devices
Many attacks exploit vulnerabilities in networking, server and end-user devices. Manufacturers respond to discovered vulnerabilities by developing and releasing updates and patches to both firmware and embedded software. Most devices do not automatically install updates, so there is human involvement needed to search for and install updates to devices. This process should be repeated at least quarterly for all infrastructure devices. Learn how to Update Firmware in Network Devices.
Software suites also regularly release updates and patches to be installed. Some are installed automatically, while others need to be manually installed. All employees should be keeping software up to date.
Use SSL VPN for Site-to-Site Connections
Virtual Private Networks (VPNs) have been a secure method to remotely connect to company resources for years. Unfortunately, most VPN software apps have vulnerabilities that can allow a hacker to gain admin access to the interface, opening it up for rogue connections to a company domain.
Upgrade to SSL VPN connections, which require an SSL Certificate be purchased and imported into each connected firewall to establish trust. New VPN software is required on end user devices to allow connection via SSL VPN.
Other permanent VPN tunnels may be used to connect a local network to a cloud hosted environment like Microsoft Azure. SSL VPN should be used here as well to protect the connection and access to the hosted environment.
See LeeShanok’s IT News articles on: SSL/TLS Migration for PCI Compliance, Work Remote Securely
Manage Firewall Ports
Firewall ports are used for computer-to-computer communication. Many firewall ports are open by default, like 443 for internet traffic. Some ports should be managed more actively, opening when network packets need to pass and then closing until the next packets need to pass.
Ports can be closed by disabling the service or using network firewall rules that Deny-All-Permit-By-Exception (DAPE). Also disabling Universal Plug and Play (UPnP) in the firewall prevents any computer in the network from opening ports without challenge.
Enabling both network firewall and host-based firewall capability is a best-practice. Enabling firewall rules will block external services, but should be tested to make sure desired services can still communicate.
On end-user computers, port management is done by antivirus apps. It’s usually fine to allow the default configuration, but some firms may have a group policy that pushes out different security policies to all end-user devices.
Set Up GeoLocation and GeoBlocking
Certain geographies are known to present greater cybersecurity risks. For example, more cyberattacks originate from China and Russia than any other countries. GeoLocation estimates where a connection originates, and GeoBlocking blocks connections from those regions.
If your company doesn’t do business in a risky geography, it should be GeoBlocked by default. Most newer firewalls have this option available.
Cloud Infrastructure and Services
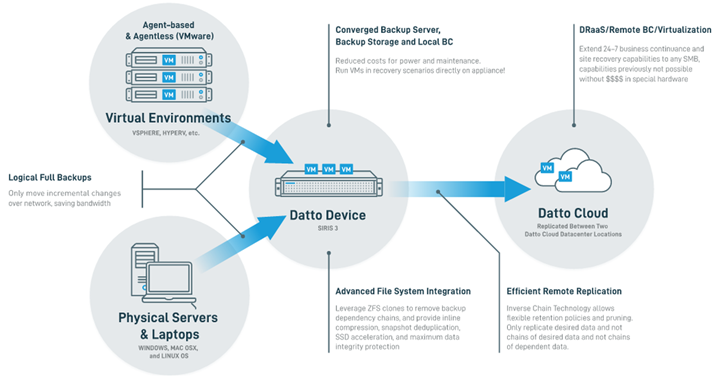
Migrate from Backups to Business Continuity & Disaster Recovery
To recover from a breach, infection or ransomware, backups are the best method. Traditional backups usually involved an external USB drive physically plugged in to a server or end user computer. This backup method may not include cloud-based data, it doesn’t protect against an on-premises disaster, and recovery may take longer.
Modern backup capability includes business continuity and disaster recovery (BCDR), which backs up operating systems, Active Directory configurations, and storage. BCDR usually involves an on-premises backup which has the ability to complete a restoration in a few minutes or hours, rather than the days or weeks a server re-build requires. There’s also a redundant cloud-based backup in the event of an on-premises disaster.
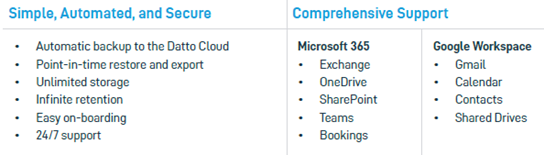
Backup your Cloud Environments
Modern backup strategies should also include important Software-as-a-Service (SaaS) accounts like Microsoft 365 or Google Workspace. Microsoft protects their data center and all data from natural disasters and failures. However, you are responsible for data loss due to human error, external hackers, malicious insiders, and more.
Approximately 90% of all companies use the cloud in some capacity and falsely assume data is backed up automatically. SaaS Protection for cloud accounts is a must-have for a modern backup strategy.

Monitor Dark Web for Compromised Company Credentials
Dark web monitoring generates reports of users in your domain whose usernames and passwords are found for sale on the Dark Web. A Dark web monitoring service can notify you when those credentials are compromised, so you can have the employee reset passwords and enable Multi-Factor Authentication.
LeeShanok offers a complimentary Dark Web Scan that shows the compromised usernames and passwords of everyone with an email address on your company’s domain.

Migrate from EDR to XDR
Endpoint Detection and Response (EDR) is the traditional method of monitoring endpoints for advanced persistent threats and new malware that may evade defenses. Extended Detection and Response (XDR) spans across platforms, endpoints, on-premises environments, cloud environments, and endpoints.
XDR usually provides a “single pane of glass” view for monitoring and responding to threats. XDR also uses artificial intelligence (AI) to scan various logs from multiple platforms and provide accurate, context-rich alerts.
Plan for Secure Access Service Edge (SASE)
SASE is a new framework in which networking and security converge into a single integrated service that works at the cloud edge to deliver networking and security functions as a service. With widespread cloud adoption, the SASE model simplifies and consolidates many different networking and security functions.
The technology is still in its early stages, but expect to adopt this model soon if your organization hasn’t yet. As an example, Cisco’s SASE offering includes:
- SD-WAN
- Cloud security
- Zero trust conditional access
- Umbrella security
- Secure access by DUO
- ThousandEyes for network outage monitoring
Hire a Managed IT Security Provider
As you can see, improving cybersecurity can be a challenging task. It requires constant vigilance and a high degree of technical expertise. Threats like ransomware are increasing every year, and businesses of every size are lucrative targets.
Many companies choose to hire managed IT service providers for their IT security. It’s generally more cost-effective, and the knowledge pool is deeper than what can be achieved with most internal IT teams. LeeShanok has been providing IT security since 1997. Request a complimentary network assessment to find out where your network is vulnerable, and which steps are most important for you to take.

Copyright © leeshanok.com
Website by CS Design Studios